The future of secure communication has arrived ! Apple has just made a major breakthrough in the world of instant messaging by integrating PQ3 post-quantum encryption into iMessage. This significant advancement offers unprecedented protection against quantum attacks, which threaten to render traditional cryptographic schemes obsolete.
What is post-quantum encryption?
Quantum computing is advancing by leaps and bounds, and with it, the threat of hacking today's encrypted data. Quantum computers, thanks to their phenomenal computing power, could break classical encryption algorithms in the blink of an eye. This is where post-quantum encryption comes in, designed to withstand these future attacks.
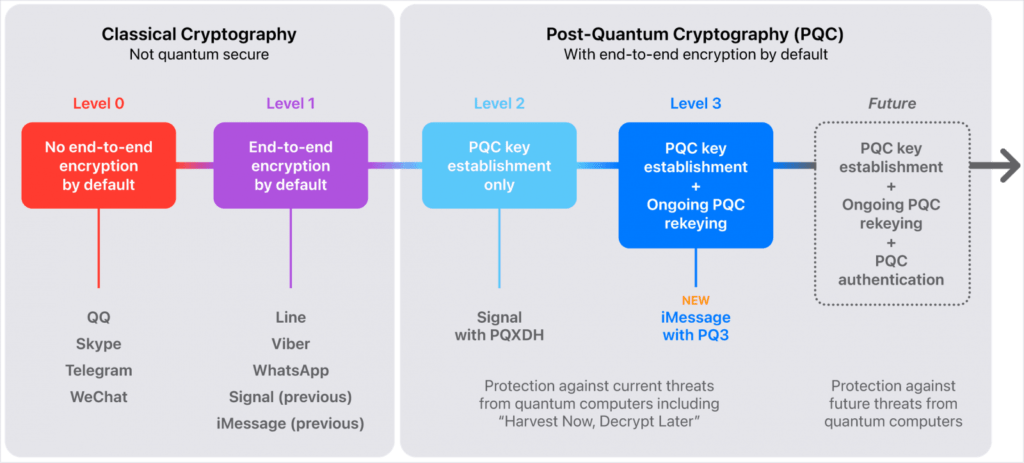
PQ3: Level 3 security for iMessage
Apple has spared no expense in ensuring the security of iMessage communications. PQ3 is not simply a replacement for the old system, but rather an addition that strengthens protection in unprecedented ways. This new protocol is the result of a collaboration with cryptography experts and is based on the Kyber algorithm, recognized by NIST for its robustness.
Revolutionary features of PQ3
- Initial key establishment : Encryption keys are created at the start of the conversation, even if the recipient is offline.
- Post-quantum periodic key change : Keys are regularly regenerated to ensure optimal security against evolving attacks.
- Recovery of compromised keys : In case of compromise, new keys are generated without affecting ongoing conversations.
A giant leap for communications security
The integration of PQ3 into iMessage is a major step forward for large-scale communication security. Apple is thus establishing itself as a leader in data protection and encouraging other market players to follow its example.
Technical operation of PQ3
PQ3 relies on a hybrid model combining the proven ECC algorithm and the new Kyber for optimal security. The encryption process consists of several steps:
- Diffie-Hellman (DH) key exchange : Devices establish a secure communication channel by exchanging public keys.
- Protocol negotiation : The devices agree on the encryption algorithms to use, including PQ3 and ECC.
- Message encryption : Messages are symmetrically encrypted with a randomly generated session key.
- Message authentication : Digital signatures guarantee the integrity and authenticity of messages.
The introduction of PQ3 in iMessage is seamless for users, meaning they don't need to take any action to benefit from its enhanced security. Security is strengthened in the background, without any interruption or impact on the flow of communications.
Here are some additional details on the impact of PQ3 on the user experience:
- Compatibility : PQ3 is compatible with current versions of iMessage on iOS and macOS. Users do not need to update their device to benefit from enhanced security.
- Performance : PQ3 was designed to be efficient and not have a significant impact on battery life or device performance.
- Privacy : PQ3 does not collect any personal or additional usage data. User privacy remains a top priority for Apple.
- Ease of use : PQ3 is easy to use and requires no special technical knowledge. Users can continue using iMessage as usual without worrying about security.
In addition to these points, here are some other aspects to consider:
- Adoption by other platforms : Apple's integration of PQ3 could encourage other messaging platforms to adopt post-quantum encryption solutions, which would help improve the security of digital communications in general.
- Future developments : The field of post-quantum cryptography is constantly evolving. Apple is committed to monitoring progress and updating PQ3 as needed to ensure optimal protection against future threats.
In conclusion, the implementation of PQ3 in iMessage is a major advancement for large-scale communication security. This Apple innovation offers robust protection against future quantum attacks without impacting the user experience.




